Client Installation
Prerequisites
BitLocker relies on the Trusted Platform Module (TPM) found in all computers available on the CPI list. By default the TPM comes turned off, disabled, and deactivated. The TPM settings are in the BIOS and the steps to turn on, enable, and activate the TPM vary by manufacturer. For the three manufacturers available on the CPI list (Dell, Lenovo, and HP) you can find instructions here on how to enable the TPM from the command line. Dell provides the most straight forward process and will probably the easiest to start with. Note, that in order to enable the TPM from the command line there needs to be a BIOS password set. If you are currently not setting a BIOS password you can set one from the command line, but it can be removed once the TPM is activated.
You also need to be running a specific version of Windows. BitLocker works with all desktop operating systems Vista and newer and must be Enterprise or Ultimate. BitLocker should not be enabled on Domain Controllers or any type of virtual machine.
Microsoft does provide a query for SCCM to identify all MBAM Supported computers. We are using that query to prescreen computers before deploying the MBAM agent.
Client Installation
Client installation is done through SCCM. The computer needs to be added to one of the ADUC security groups for MBAM SC:
<OU>-SC-Microsoft-MBAM-BitLocker Settings Normal
<OU>-SC-Microsoft-MBAM-BitLocker Settings High
Most computers on campus can be added to the Normal group. The Normal group requires no end user interaction beyond what is needed to enable the TPM. The High option are for users who might have sensitive data on their machine. The High option will require the users to set a boot PIN. The boot PIN will need to be enter before the operating systems starts.
The BitLocker settings are applied through a GPO. After a machine is added to the OS group run gupdate /force from a command prompt and reboot the computer.
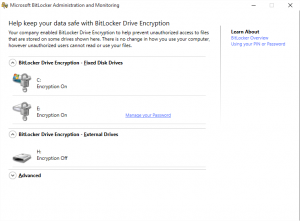
Both groups use AES-256 to encrypt drives and recovery keys are stored in the BitLocker database as well as AD. Both settings will encrypt the OS drive as well as any fixed drive in the computer. Fixed drives are set to auto unlock at boot time. Meaning if the OS can boot successfully there are not additional steps needed to access data on fixed drives.
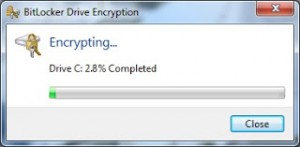
Encryption times vary depending on the size of the drive and processor speed of the computer. The encryption process takes place in the background and the end user should see no performance issues during the encryption process. Fixed drive encryption begins AFTER the OS drive is fully encrypted. While computers are encrypting they can be put to sleep, rebooted, and powered off. Encryption will resume when the computer is turned back on. During proof of concept we tested what would happen if a computer lost power during encryption by unplugging a computer’s power. Once powered was restored encryption resumed with no loss of data.
After the MBAM agent is installed there is an item added to the Control Panel to monitor the status of BitLocker on the computer.
Control Panel -> System and Security -> BitLocker Encryption Options
MBAM also creates a service called BitLocker Management Client Service.
A new set of logs is created in the Event Viewer.
Event Viewer -> Application and Services Logs -> Microsoft -> Windows -> MBAM
There are two logs, Admin and Operational. The Admin log provides errors if the MBAM client has problems talking to the MBAM servers. The Operational log provides information about applying policy, escrowing of keys, and encryption status being successfully sent.
Encrypting
For encryption to begin someone must be logged in at the console (locally). Encryption will not begin if a user is RDP’d to a computer. The MBAM client checks in and reports its status every 15 minutes. A user must be logged into the computer for at least 15 minutes before encryption will begin.
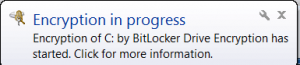
Once encryption begins users will receive a popup from the system tray informing them encryption has begun.
From the system tray users can also get the status of the encryption process by double clicking on the BitLocker icon.
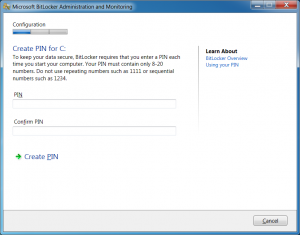
For users in the High option, a boot PIN must be set before encryption can begin. Due to the interactive nature of the High option users are given a 14 day grace period in which encryption can be postponed. After 14 days the BitLocker PIN creation wizard cannot be canceled or minimized.
Other Information
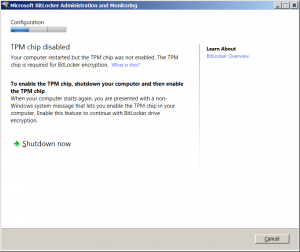
If the TPM is on in the BIOS but not enabled the user may get a message saying the TPM chip is disabled and a reboot is needed to continue.
Depending on the computer and BIOS version when the computer reboots a non Windows message will be displayed asking the user to enable the TPM select F10.
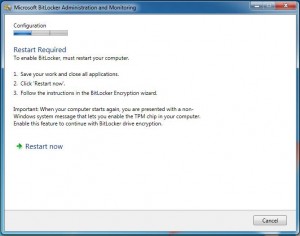
If the TPM is on and enabled but not activated the user may be presented with the following message.
Depending on the computer and BIOS version when the computer reboots a non Windows message will be displayed asking the user to activate the TPM select F10.