Windows LAPS
Windows LAPS is a technology that automatically randomizes a local user account’s password and escrows the password on the computer object in Active Directory or, for Intune managed devices, on the device identity in Entra ID. All university-owned computers joined to the Wolftech domain, at or below the NCSU OU or enrolled in Intune are in scope to receive policy that configures Windows LAPS.
In our environment, the well-known local administrator account’s password is managed by LAPS. We do rename the account to wolftech.admin but a department may use their own group policy to change the name to something that’s a better fit.
Only departmental OU admins group, NCSU OU admins, and domain admins can read the LAPS password for the department’s computers.
Windows LAPS will automatically change the local user account’s password after 90 days unless the password has been used. Once used, the password will be changed in 12 hours.
Retrieving a LAPS password
If a departmental IT administrator needs to sign in to a computer with the local administrator account, they can retrieve the password using Active Directory Users and Computers (ADUC) or PowerShell.
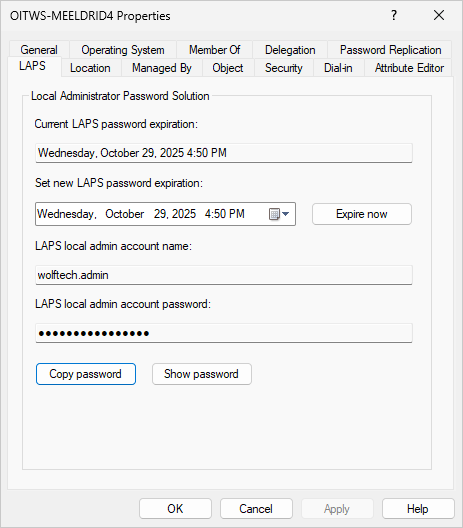
Active Directory Users and Computers
Locate the computer object in your OU and double click it or right-click and select Properties. The LAPS tab should be visible whether or not the Advanced Features view is enabled.
PowerShell
Run the Get-LapsADPassword cmdlet.
Get-LapsADPassword -Identity <COMPUTERNAME> -AsPlainTextLegacy LAPS
We moved to Windows LAPS from what is now referred to as Legacy LAPS. Legacy LAPS required the installation of a client application where Windows LAPS is built in to Windows and does not require a client application. The Legacy LAPS attributes and password will remain on computer objects along with the most recent escrowed password. This is mostly to deal with cases where a computer has been offline for a while and departmental IT may need the Legacy LAPS password to sign in with the local administrator account because signing in with a domain account isn’t working.
Windows LAPS uses a different location in the registry for its settings than what Legacy LAPS uses. The attributes on the Active Directory computer object are also different.
| Legacy LAPS | Windows LAPS | |
|---|---|---|
| Requires client application | Yes | No |
| Registry settings location | HKLM\Software\Policies\Microsoft Services\AdmPwd | HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\LAPS |
| AD computer attributes | ms-Mcs-AdmPwd* | msLAPS-* |
The Legacy LAPS attributes and password will remain on the computer object in case a computer that has been offline for a while, and is unable to authenticate to the domain, can be signed in to.
Logging
The Windows LAPS event log is located at Microsoft-Windows-LAPS/Operational. Policy processing log entries should be added hourly.