Software Restriction
Software Restrictions Policies are available in Windows 7, XP, Vista, Servers 2003 and 2008. They are found under Computer Configuration\Windows Settings\Security Settings\Software Restriction Policies node of the local group policies. In a network setup with domain controllers you would edit the Domain Group Policy but for a single computer system edit the Local Group Policy by typing gpedit.msc in the Start search text box.
Software restrictions are based on rules which are applied in a particular order. Specific rules override the general ones and the order is as follows:
- Hash rules (most specific)
- Certificate rules
- Path rules
- Zone rules
- Default rules (least specific)
When conflicts occur the most specific rule takes precedence. For example, if the Default rule for application A is set to as Disallowed while a Hash rule is set to as Unrestricted then Application A will execute normally since the hash rule is more specific.
Default Rules
Default rules are found in the Security levels node under the Software Restriction Policy. The security levels define the default behavior of applications execution if no other specific rule matches. Default rules can be set as follows:
- Disallowed: blocks users from executing an application by default – others specific rules may override this one.
- Basic User: allows users to execute applications that do not require administrative privileges – to allow users to run applications with administrative privileges a specific rule must be created.
- Unrestricted: users are able to execute an application by default – others specific rules may override this one.
Common sense dictates that in an environment where all applications are blocked by default and only specific ones are allowed, a disallowed default rule would be more appropriate. While, if an organizations requires a mechanism where only few specific applications need to be blocked then an Unrestricted default rule would be more appropriate.
Enforcement
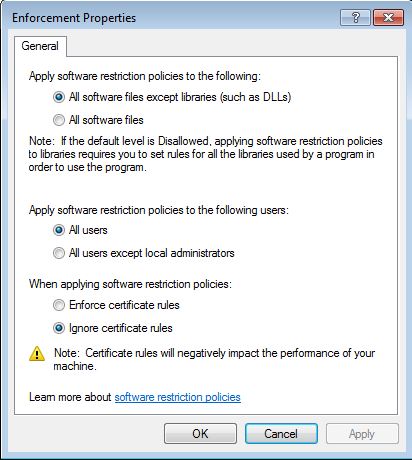
The Enforcement Properties policy allows you to specify whether to apply default rules to all files including libraries or all files excluding libraries such as DLLs. When including all libraries and the default policy is set Disallowed then, you need to set specific rules for all those libraries that are required by unrestricted applications, otherwise they would not run. It is recommended to exclude libraries when the default policy is set to Disallowed unless there are specific reasons such as, in a highly controlled environment.
A practical setting in the enforcement properties policy is the exclusion of local administrators from the rules. If the Apply software restriction policies to the following users: is set to All users except local administrators then members of the local administrators group are permitted to run disallowed applications.
The last option is to enforce certificate rules. As this option has a negative impact on performance it is recommended to ignore it.
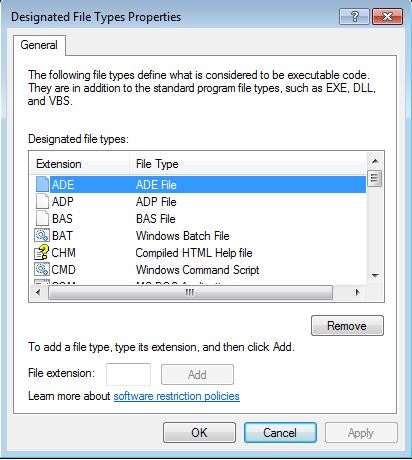
Designated File Types
This option allows you to add executable files with uncommon extensions to the executable group of files. The tool lists the most popular extensions of executables such as, .exe, .com, .vms, etc. Hence, these file types are considered as executable code and would fall under the check of the Software Restriction Policies. If the required executable extension does not exist in the provided list of extension types then add your own specific extension types from the Add button.
Path Rules
Additionally, you can add files, folders and registry keys as specific entries that would fall under the Software Restriction policy. For example, you set an entire folder that contains several executables to Disallowed and therefore, all executables will not run! Later on, you may need to allow one of the executables to run. In such cases, you just need to add another specific path to this executable and set it as Unrestricted. Since the second path is more specific it takes precedence over the first entry. Wildcards can be used and they are considered as less specific than the full path.
An important feature of Path Rules is that you cannot set path rules to folders and files that can change location. The policy gets this information from the NTFS permissions. If such permissions allow a file or folder to be moved or renamed then there is no point in setting a Software Restriction Policy.
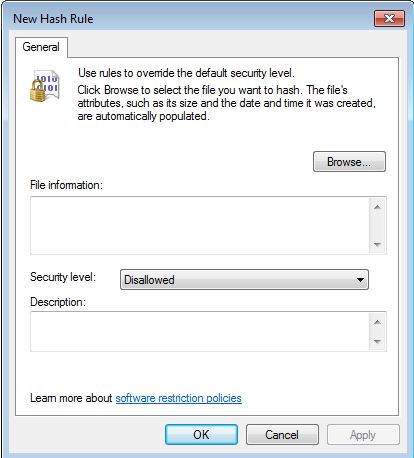
Hash Rules
If the Path Rules had a location or rename restriction, Hash Rules overcome this by applying a hash rule over a file which makes it identifiable from any location or name assigned to it. Such hash is generated from the binary characteristics of a file and a digital fingerprint is generated. There are various drawbacks when using hash rules. They are specific to files and if you need to hash many files you need to perform the action on each file. You have to cater for this when upgrading applications that are set with hash rules. Since, updates may alter these files by changing their digital fingerprint, as a consequence the hash rule then fails. You would need to reset all files hash rules affected by the update.
Certificate Rules
Similar to the option of enforcing certificate rules within the Enforcement Properties, this rule also degrades the execution of applications as the certificate validity must be checked every time the application is executed. Certificates are obtained from the application vendor and it is not necessary to modify the rule whenever the application is updated as the vendor’s certificate remains valid. Hence, using certificate rules allows you to create a rule that applies to a group of applications (from the same vendor) as opposed to Hash rules where you need to create a rule for each and every executable you want to restrict or allow. On the other hand, you hit trouble if you want to restrict just one application out of many unrestricted executables from the same vendor. Then, certificate rules cannot be used in this scenario.
Network Zone Rules
This rule applies to Windows Installer packages and which may be downloaded through the Internet explorer. Other downloaded files are excluded from this rule. Rules are based on zones that contain Web sites as set in the locations Internet, Local intranet, Restricted sites, Trusted sites and Local Computer.